In recent years, there was a concerning trend of criminals making use of superior generation to useful resource of their illegal activities. One such rising fashion is the use of mobile and Wi-Fi jammers via thieves to advantage get admission to to houses for robbery. This article delves into the mechanics of cell and Wi-Fi jammers, explores how criminals are exploiting them, and discusses the risks related to this alarming fashion.
Introduction to Cellular and Wi-Fi Jammers


What are Cellular Jammers?
Cellular jammers, also known as sign blockers or signal jammers, are electronic devices designed to disrupt the verbal exchange among mobile phones and their respective cell base stations. They perform by using emitting radio frequency indicators on the identical frequency bands used by cellular phones, correctly blockading incoming and outgoing calls, text messages, and cell internet connectivity within a certain radius.
What are Wi-Fi Jammers?
Wi-Fi jammers, then again, goal wi-fi nearby place networks (Wi-Fi) by way of emitting radio indicators that intrude with the everyday functioning of Wi-Fi routers and get entry to factors. By disrupting Wi-Fi indicators, those jammers prevent devices connected to the network from having access to the internet or speaking with every different wirelessly.
Emerging Trend: Thieves Using Jammers for Robbery


Instances of thieves employing cellular and Wi-Fi jammers as tools for housebreaking had been pronounced throughout various areas. Criminals were acknowledged to apply jammers to disable safety structures that depend upon cellular or Wi-Fi connectivity, consisting of alarm structures, CCTV cameras, and clever locks, thereby gaining unauthorized get admission to to properties with minimum resistance.
How Cellular and Wi-Fi Jammers Work
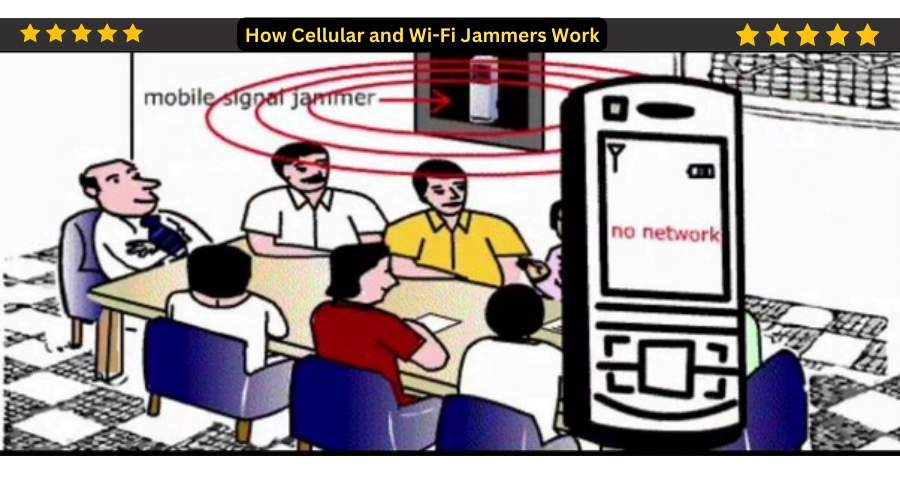

Mechanism of Cellular Jammers Cellular jammers function by using transmitting excessive-electricity radio alerts at the identical frequencies used by cellular networks, correctly overpowering and disrupting the valid indicators exchanged between cell phones and cell towers. This interference renders cell gadgets inside the area incapable of setting up or retaining a stable connection to the cellular community.
Mechanism of Wi-Fi Jammers Wi-Fi jammers operate further to cellular jammers but goal Wi-Fi networks instead. These gadgets emit radio alerts on the equal frequencies as Wi-Fi routers, causing interference that disrupts the normal operation of wireless net connections. As a end result, devices within the affected vicinity are not able to hook up with the Wi-Fi community or enjoy vast degradation in internet speed and reliability.
Risks Posed by Thieves Using Jammers


The proliferation of cellular and Wi-Fi jammers poses widespread risks to both residential and business protection systems.
Disruption of Communication Systems By jamming cell and Wi-Fi indicators, thieves can successfully neutralize safety features that depend on those conversation technology. This consists of disabling alarm structures that use mobile networks to communicate signals to monitoring centers and disrupting Wi-Fi-primarily based surveillance cameras that provide actual-time video tracking of houses.
Impact on Security Systems The use of jammers can undermine the effectiveness of advanced protection structures, which includes smart locks and domestic automation structures, which depend on uninterrupted connectivity to feature well. Thieves can exploit these vulnerabilities to bypass safety features and benefit unauthorized access to homes and groups, increasing the chance of a success burglaries.
Ways to Counteract the Threat


To mitigate the chance posed by thieves the usage of mobile and Wi-Fi jammers, proactive measures should be taken at both person and regulatory levels.
Advanced Security Measures Implementing multifaceted safety solutions that contain redundant verbal exchange channels can assist mitigate the impact of sign jamming assaults. This consists of deploying security systems that utilize multiple communique technologies, together with cellular, Wi-Fi, and landline connections, to make sure resilience against jamming attempts.
Legal Regulations and Enforcement Governments and regulatory bodies play a crucial position in combating the illicit use of signal jammers. Enforcing strict guidelines on the sale, possession, and use of jamming gadgets can deter criminals from using them for nefarious functions. Additionally, law enforcement businesses have to actively check out and prosecute people concerned in the unlawful distribution and operation of jamming device.
Thieves Using Cellular and Wi-Fi Jammers to Enter Homes for Robbery


On the night of February 16, an normal Friday night time took a startling turn for my husband and me. Opting for a relaxed nighttime in, we planned a simple dinner of grilled chicken and salad. However, our tranquil evening was unexpectedly interrupted round 6:forty five p.M. Through the ominous sound of rumbling overhead.
Stepping onto our again patio, we have been met with an sudden scene: two police helicopters hovered ominously above, their searchlights casting an eerie glow over our property. In the midst of the clamor, a bone-chilling proclamation echoed thru the night time air, “Police. You are under apprehension. Remain stationary and there can be no want for in addition movement.”
Peering over the fence, we witnessed a swarm of armed Phoenix SWAT Team participants, followed through vigilant dogs, encircling our home. Confusion gripped us as we inquired about the situation, handiest to be directly told to retreat interior with the aid of the government.
It turned into then that a member of the SWAT crew approached me with a grave revelation. “Ma’am, a South American gang is concentrated on homes within the vicinity,” he explained, gesturing closer to a mysterious tool in his hand. “The jammer indicates you would possibly had been their next goal. Do we have your permission to conduct a search?”
With a aggregate of alarm and gratitude, I consented, promising full cooperation in apprehending any intruders. As gates had been opened and security features bypassed, we learned the chilling fact: had the group now not detected our presence, our fate may have mirrored that of our unlucky pals.
Indeed, only a few doors down, a owner of a house fell victim to the ruthless performance of these criminals. Leaving for dinner at five p.M., he remained oblivious to the upcoming risk until his safety cameras mysteriously went offline. In a brazen act of housebreaking, the gang made off with a widespread sum of cash and valuables, leaving devastation of their wake.
But how do they retain to keep away from justice? The solution lies in their sophisticated tactics. By deploying mobile and Wi-Fi jammers, they render protection structures and conversation devices vain, operating with impunity underneath the quilt of darkness.
Yet, amidst the chaos, a glimmer of resilience emerged. Our home, equipped with tough-stressed safety cameras and a reliable landline, stood as a beacon of defiance against those technological disruptions. And even as the ordeal changed into harrowing, it served as a sobering reminder of the significance of vigilance and preparedness within the face of emerging threats.
As the dirt settled and gratitude flooded our hearts, I could not help but reflect at the broader implications of this incident. This turned into now not an isolated occasion however alternatively a symptom of a pervasive issue plaguing communities nationwide. From Phoenix to California, those brazen acts of criminal activity spare no one, transcending geographical boundaries with impunity.
In the aftermath of this ordeal, one reality stays abundantly clear: the tireless efforts of law enforcement are critical in safeguarding our houses and communities. To them, we owe a debt of gratitude for his or her unwavering dedication and fast action in thwarting these nefarious schemes.
In the end, our brush with danger serves as a poignant reminder that in an increasingly interconnected world, vigilance is our greatest defense against the forces of darkness. And as we continue to navigate the complexities of modern life, let us remain ever vigilant, united in our resolve to protect that which matters most—our safety, our security, and our peace of mind.
Conclusion
The growing trend of thieves using cellular and Wi-Fi jammers to facilitate robberies underscores the need for heightened awareness and proactive security measures. By understanding the mechanics of these devices and implementing appropriate countermeasures, individuals and authorities can mitigate the risks associated with signal jamming attacks and safeguard against unauthorized intrusions.
FAQs(Thieves Using Cellular and Wi-Fi Jammers to Enter Homes for Robbery)
Can cellular and Wi-Fi jammers be legally purchased for legitimate purposes?
In most countries, the sale and use of cellular and Wi-Fi jammers are illegal due to their potential for disrupting vital communication networks. However, some jurisdictions may permit their use by authorized government agencies for specific applications such as law enforcement or military operations.
How far-reaching is the impact of signal jamming attacks?
The range of cellular and Wi-Fi jammers can vary depending on various factors such as the device’s power output and environmental conditions. In optimal conditions, jammers can disrupt signals within a radius ranging from a few meters to several hundred meters.
Are there any technologies that can detect and counteract signal jamming attacks?
Yes, there are specialized technologies designed to detect and mitigate the effects of signal jamming attacks. These include signal monitoring systems that can identify unusual interference patterns indicative of jamming activity and adaptive security solutions that automatically switch to alternative communication channels in the event of signal disruption.
What are the legal consequences of using cellular and Wi-Fi jammers for illegal purposes?
Engaging in the unauthorized operation of signal jammers can result in severe legal penalties, including fines, imprisonment, and confiscation of equipment. Individuals found guilty of using jammers for criminal activities may also face additional charges related to burglary, trespassing, or sabotage.
How can homeowners protect their properties against signal jamming attacks?
Homeowners can enhance their security measures by investing in integrated security systems that incorporate diverse communication technologies and implementing physical deterrents such as reinforced doors and windows. Regularly updating security protocols and staying informed about emerging threats can also help mitigate the risk of burglary attempts facilitated by signal jammers.
Do burglars use WiFi jammers?
WiFi jammers can potentially be used by burglars to disrupt wireless signals and hinder security systems. However, the prevalence of such usage is not widely reported.
Do criminals use jammers?
Criminals may employ various types of jammers to interfere with communication systems, including WiFi and cell phone signals, for nefarious purposes such as avoiding detection or disrupting security measures.
What do people use WiFi jammers for?
WiFi jammers are sometimes used by individuals for purposes such as maintaining privacy, blocking unwanted network access, or conducting experiments. However, their use can also be illegal and disruptive.
Are WiFi jammers legal?
In many jurisdictions, the use of WiFi jammers is illegal as they interfere with authorized radio communications. Unauthorized operation of jammers can lead to legal consequences.
Do burglars use cell phone jammers?
- Cell phone jammers can potentially be used by burglars to disrupt cellular communication within a targeted area, preventing communication with emergency services or security personnel.
Can a jammer block mobile data?
Yes, certain types of jammers can disrupt mobile data transmission by blocking or interfering with the radio signals used for data communication.
Can cellular cameras be jammed?
Cellular cameras, like any other wireless devices, can be susceptible to jamming if their communication signals are disrupted by a jamming device operating within the vicinity.
What is the most powerful jammer?
The power and effectiveness of a jamming device can vary depending on its design and specifications. There isn’t a single “most powerful” jammer, as different jammers may be optimized for disrupting specific types of signals or operating in different environments.
Can burglars disable WiFi?
Yes, burglars can potentially disable WiFi networks by using WiFi jammers or by physically damaging or tampering with the networking equipment.
Can a jammer block CCTV?
Certain types of jammers may interfere with the wireless signals used by CCTV cameras, rendering them unable to transmit video footage or disrupting their operation.
Why use a cell phone jammer?
Cell phone jammers may be used for purposes such as maintaining privacy, preventing unauthorized phone use in certain areas, or disrupting communication during events or protests. However, their use is often illegal and can pose risks to public safety.
Are jammers harmful to humans?
While jammers themselves may not pose direct physical harm to humans, their use can have unintended consequences such as disrupting emergency communication systems or interfering with medical devices that rely on wireless signals.
Can jammers be detected?
Detecting jammers can be challenging, but specialized equipment and techniques exist for identifying and locating the source of jamming signals. However, the effectiveness of detection methods may vary depending on the sophistication of the jamming device.
Is there a jammer detector?
Yes, there are devices designed to detect and locate the presence of jamming signals within a given area. These detectors work by analyzing radio frequency interference and can help identify unauthorized jamming activity.
Are jammers detectable?
While jammers themselves may not always be easily detected, their effects on wireless communication systems can often be observed through signal analysis and monitoring techniques, allowing for the detection and mitigation of jamming activity.


TotalInfo4U: Your Ultimate Source for Comprehensive Knowledge

